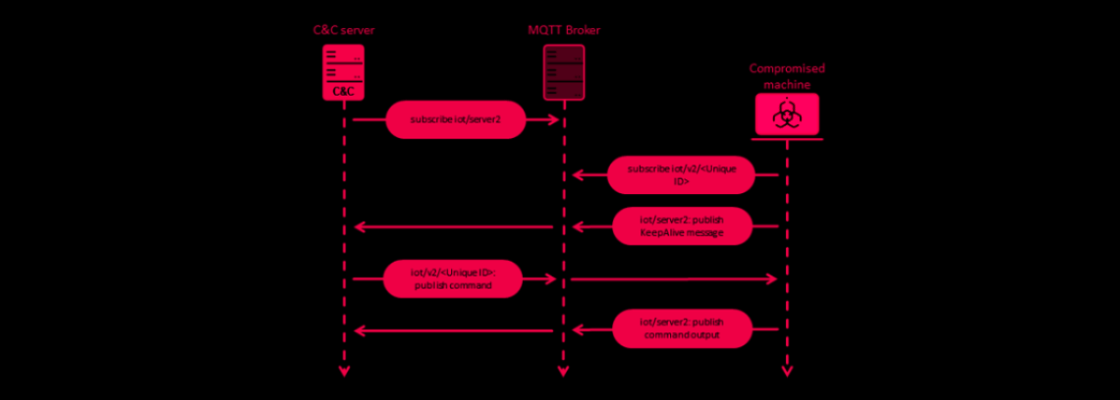
Hackers targeting European entities with MQsTTang backdoors
The Mustang Panda actor, which is aligned with China, has been observed using a new custom backdoor named MQsTTang as part of an ongoing social engineering campaign that started in January 2023. ESET researcher Alexandre Côté Cyr reported that MQsTTang seems to be a standalone backdoor not based on existing malware families or publicly available
- Published in News
A new variant of the SysUpdate malware attacks Linux and employs evasion tactics
The threat group known as Lucky Mouse has released a Linux version of its SysUpdate malware toolkit, enabling it to target Linux devices. The updated artifact, which dates back to July 2022, has new features aimed at avoiding security software and resisting reverse engineering. Lucky Mouse, also known as APT27, Bronze Union, Emissary Panda, and
- Published in News
Users are vulnerable to command injection attacks due to a critical flaw in Cisco IP Phone Series
On March 1, 2023, Cisco released security updates for its IP Phone series 6800, 7800, 7900, and 8800 to address a critical command injection vulnerability (CVE-2023-20078) rated 9.8 on the CVSS scoring system. The flaw is caused by a web-based management interface, which lacks proper user-supplied input validation, allowing an unauthenticated, remote attacker to inject
- Published in News
Trojanized macOS apps are used by hackers to distribute cryptocurrency mining malware
Jamf Threat Labs has discovered that Trojanized versions of legitimate applications are being used to deploy evasive cryptocurrency mining malware on macOS systems. The malware, called XMRig coin miner, is executed by an unauthorized modification in Final Cut Pro, an Apple video editing software. The malware makes use of the Invisible Internet Project (i2p) to
- Published in News
Apple warns of three new vulnerabilities affecting iPhones, iPads, and Macs
Apple has released revised security advisories to address three new vulnerabilities that could impact iOS, iPadOS, and macOS. One of the vulnerabilities is a race condition in the Crash Reporter component that could allow a malicious actor to read arbitrary files as root, while the other two vulnerabilities in the Foundation framework could be weaponized
- Published in News
Norway confiscates $5.84 million worth of cryptocurrency stolen by Lazarus hackers
The Norwegian police agency Økokrim has announced the seizure of $5.84 million worth of cryptocurrency, which was stolen by the Lazarus Group in March 2022 after the Axie Infinity Ronin Bridge hack. The Oslo-based crime-fighting unit stated that this case highlights its capacity to trace the money trail on the blockchain, even when criminals use
- Published in News
Open Source Antivirus Software ClamAV Detected with Critical RCE Vulnerability
Cisco has recently released security updates to address a severe vulnerability in the ClamAV open-source antivirus engine, which could result in remote code execution on susceptible devices. The vulnerability is tracked as CVE-2023-20032, with a CVSS score of 9.8, and it pertains to remote code execution in the HFS+ file parser component. Versions 1.0.0 and
- Published in News
New M2RAT malware from North Korea’s APT37 targets South Korea
The notorious APT37, a North Korea-linked threat actor, has recently been spotted utilizing a new piece of malware called M2RAT in its ongoing attacks against its southern neighbor. These developments signify a further evolution of the group’s tools and tactics. APT37, also known as Reaper, RedEyes, Ricochet Chollima, and ScarCruft, is associated with North Korea’s
- Published in News
Thousands of WordPress sites have been infected by a massive AdSense fraud campaign
The malicious black hat redirect malware campaign has now grown larger and more insidious, infecting over 10,800 websites with over 70 bogus domains, mimicking URL shorteners. The main objective of this malware is to artificially increase traffic to pages that contain Google Ads, generating revenue from AdSense ID, which is used for ad fraud. The
- Published in News
Massive HTTP DDoS Attack Hits Record High of 71 Million Requests Per Second
Cloudflare, the web infrastructure company, stopped an unprecedented DDoS attack on Monday with a record-breaking peak of over 71 million requests per second. This historic “hyper-volumetric” attack was the largest HTTP DDoS attack on record, surpassing the previous 46 million RPS attack that was mitigated by Google Cloud in June 2022. These massive attacks targeted
- Published in News