The Mustang Panda actor, which is aligned with China, has been observed using a new custom backdoor named MQsTTang as part of an ongoing social engineering campaign that started in January 2023. ESET researcher Alexandre Côté Cyr reported that MQsTTang seems to be a standalone backdoor not based on existing malware families or publicly available projects. The group has increased its attacks on European entities since Russia’s full-scale invasion of Ukraine in 2022.
While the victimology of the current activity is unknown, ESET stated that the decoy filenames are similar to those of the group’s previous campaigns targeting European political organizations. However, ESET has also observed attacks against unknown entities in Bulgaria and Australia, as well as a governmental institution in Taiwan, indicating a focus on Europe and Asia.
Mustang Panda has a history of using PlugX for remote access, but recent intrusions have shown that the group is expanding its malware arsenal to include custom tools like TONEINS, TONESHELL, and PUBLOAD. In December 2022, Avast reported another set of attacks on government agencies and political NGOs in Myanmar that resulted in the exfiltration of sensitive data using a PlugX variant called Hodur and a Google Drive uploader utility.
An FTP server associated with the threat actor has been found to host several previously undocumented tools used to distribute malware to infected devices, including a Go-based trojan called JSX and a sophisticated backdoor referred to as HT3. The development of MQsTTang indicates a continuation of this trend, even though it is a “barebones” single-stage backdoor that allows for executing arbitrary commands received from a remote server, without any obfuscation techniques.
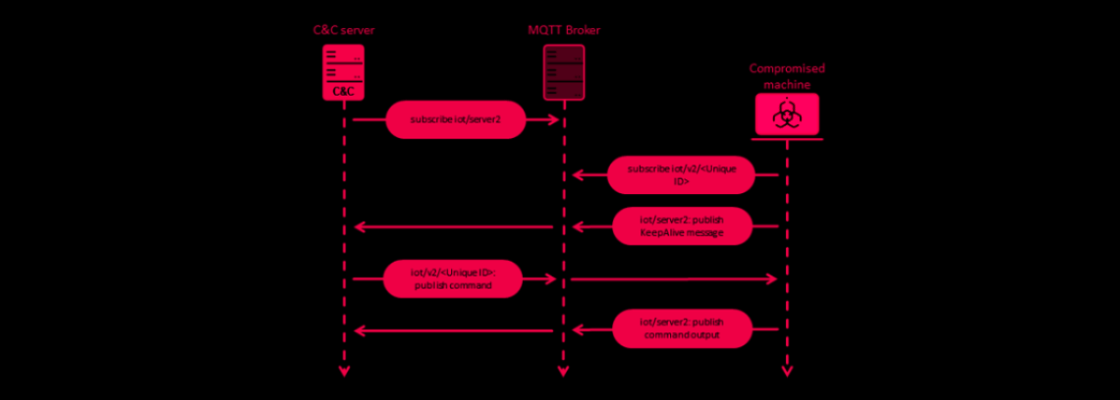
However, what’s unusual about this implant is that it uses an IoT messaging protocol called MQTT for command-and-control (C2) communications, which is accomplished using an open-source library called QMQTT, an MQTT client for the Qt cross-platform application framework. The attacks’ initial intrusion vector is spear-phishing, with MQsTTang distributed via RAR archives containing a single executable featuring filenames with diplomatic themes.
ESET researcher Côté Cyr stated that “This new MQsTTang backdoor provides a kind of remote shell without any of the bells and whistles associated with the group’s other malware families. However, it shows that Mustang Panda is exploring new technology stacks for its tools.”




